摘要: As we spend more of our lives online, the security of our private data is an increasingly salient concern.

▲來源:medium.com
It’s Time for New Approaches to Identity Verification
Two days ago, Quora announced that up to 100 million users’ data were compromised by hackers in an attack last week. The data may have included a user’s name, email address, encrypted (hashed) password, and data imported from linked networks authorized by users.
Last week, Marriott revealed a massive database breach that leaked personal info on up to 500 million guests. In September, hackers stole personal information from 29 million Facebook accounts. High-profile cases such as Equifax and Cambridge Analytica are increasingly seen as strategic and political risks — the size, frequency, and impact of these data breaches have increased year over year for the past decade, and show no signs of abating.
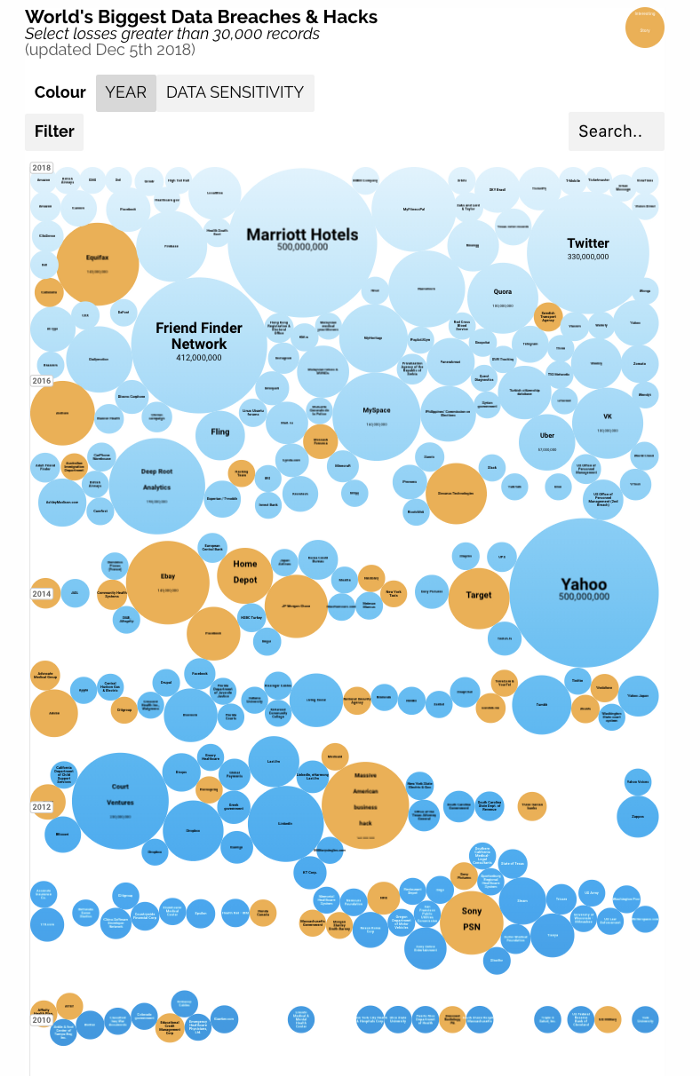
▲Source: World’s Biggest Data Breaches
As we spend more of our lives online, the security of our private data is an increasingly salient concern. Companies like Google, Facebook, Amazon, Baidu, and other big tech platforms have a near-monopoly on our data, and they store it in centralized databases. These single points of failure make them vulnerable targets for hackers. It is no surprise, therefore, that many people have high expectations for blockchain technology as a compelling solution to problems in the digital identity services sector.
Metaverse Avatars: Secure, Self-Sovereign Digital Identity
Open standards are a core design principle of blockchain protocols, which have emerged at just the right time in the IT market cycle to challenge incumbents. Blockchain and distributed ledger technology offer a number of advantages over the centralized databases in widespread use today, including cost savings, security, and transparency. We expect that in the future, blockchain-based digital identities will force the current big tech “data monopolies” to either change their business model, or be supplanted entirely.
▲Source: Placeholder VC
For individual users, one way in which blockchain can improve the online experience is through secure, convenient logins. Currently, when users want to login to an online service they must register an account for each website using an email address and password. This process is cumbersome and/or insecure: it is difficult to remember numerous unique passwords without a password manager, and using the same password for multiple logins is risky. Thus, many websites offer a “social login” option in which the user can link his or her account to another verified account, such as Facebook, Google, LinkedIn, or Twitter. The problem is, if Facebook or Google leak users’ data, every linked account is also compromised.
Moreover, the data associated with online accounts no longer belong to the user. Without exception, “free” online services are not really free; your personal information and usage data are sold to advertisers and the Cambridge Analyticas of the world.
What if there was a way to securely access all the websites and digital services you need online, without the risk of data breaches and without tech giants profiting from selling your “digital footprint”?
In the Metaverse blockchain, digital identities (Avatars) allow users to create a unique identifier that can be used to login and access any application within the Metaverse ecosystem. The Avatar is built into the protocol level and linked to a user’s public address. To link the Avatar to a Metaverse wallet requires a one-time, low-cost transaction, effectively ensuring that the user is not a bot. In the next Metaverse update, attributes will be attached to the Avatar, allowing a publicly viewable reputation system to track users’ network activities, such as community involvement, investment and mining activity, and transactions. This allows other users to verify, with a high degree of certainty, that another user is a real person.
The main advantage of incorporating digital identity into the protocol layer is interoperability: Metaverse Avatars have a unified standard that is automatically recognized by all the applications on the platform. Eventually, this digital identity standard will evolve into a decentralized know-your-customer (KYC) system which can be used as a universal login. Personal identification data can be verified by intermediaries known as Oracles, who write attestations to the blockchain. Attestations of an Avatar’s credentials, in turn, can provide other users a high degree of confidence that a user is real and trustworthy, without revealing private data or storing it on the blockchain or a central database.
轉貼自: medium.com
若喜歡本文,請關注我們的臉書 Please Like our Facebook Page: Big Data In Finance

留下你的回應
以訪客張貼回應